What is security testing?
Security testing is a non functional testing process used to determine that the data contained in an information system is secure and protected. Security testing also verifies that only authorized users can login to the system and there is no information leakage. We use a wide range of software, hardware and firewalls like metaspoilt, wireshark, w3af, netsparker, ZED attack proxy (ZAP) etc.
Why do we need security testing?
- To gain customer trust
- To avoid revenue impact
- To avoid website downtime
- To reduce cost by securing the application against future attacks
Principles of Security Testing
- Authentication: The system should validate that the data used by the system is genuine.
- Authorization: Specific users should only be given access to authorized functions.
- Confidentiality: Data inside the systemshould be secured from theft.
- Integrity: The application data is not altered in course of time.
- Non-repudiation: Once data is send or received, the sender or receiver of the information cannot deny it.
Common security threats and techniques
- SQL Injection: Malicious SQL statements are used to get critical information from the database by inserting them to the text fields or url. SQL injection can also grant unauthorized access.
For example: If a user gets a database error on submitting single quotes, it means that some query input is executed by the application. Ideally it should be validated and rejected by the application.
- Cross site scripting(XSS): Through XSS, attackers can inject client side script into webpages and make the user to click on that link. Any HTML <html> or Script <script> should be rejected by the application.
- URL Manipulation: Attackers manipulate the website URL strings to modify the GET method which pass information between client and server. Such modified requests will capture important information from the server. Under such attacks user may also get access to unauthorized pages.
- Brute force attack: Using automated software (e.g. Jmeter), we can try out a large combination of username and passwords to get access to the system. A secure system should prevent repeated and frequent login attempts.
ZAP Penetration Testing
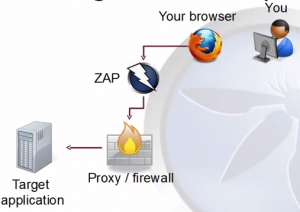
ZAP (Zed attack proxy) is an open source penetration testing tool maintained by the Open Web Application Security Project (OWASP) to know the vulnerabilities in web applications. It stands between the tester’s browser and the web application so that it can intercept and inspect messages sent between browser and web application, modify the contents if needed, and then forward those packets on to the destination.
Using ZAP, we can perform three types of automated scanning;
- Passive scanning – Passive scanning spiders your web-app and scans the responses without altering them. Only potential hazards can be detected by passive scanning
- Active scanning – By active scanning, we can both scan and attacks the web-application
- Fuzzing – Fuzzing allows us to modify the response from the web-app and view the results instantly
How to download and run OWASP ZAP?
- Download the tool from the link https://github.com/zaproxy/zaproxy/wiki/Downloads
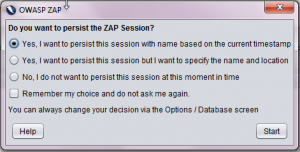
- Session Persisting: Whenever we start ZAP, we will be asked if we want to persist ZAP session. The ZAP sessions are saved to database with a name and location by default. If we do not persist the session, the session files will be automatically deleted on exiting the app.
- Set up Proxy in ZAP.
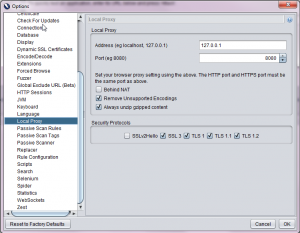
Before setting up proxy in ZAP, don’t forget to clear all active sessions in Firefox browser. After clearing all sessions, go to ZAP tool >> Tools Menu >> Options >> Local Proxy. Change address to 127.0.0.1 and port as 8080.
- Now, access the url of the web-application using Firefox browser and when successfully connected, there will be more lines under ‘sites’ and ‘history’ tabs.
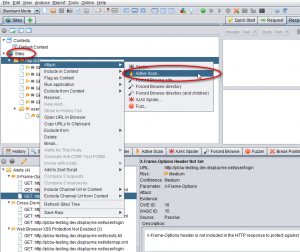
- Now the attack can be activated by right clicking the HTML folder and clicking ‘activate scan’ under ‘attack’ menu.
Run a Quick Start Test
To run a Quick Start test, Access the Quick Start tab of the Workspace Window and enter the URL in the attack text box. Then click the attack button. ZAP will proceed to crawl the web application with its spider, then passively scan each page it finds. The spider looks through all the responses for the vulnerabilities. Then ZAP will use the active scanner to attack all of the discovered pages, functionality, and parameters.
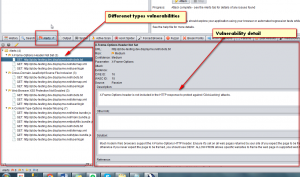
The security issues found by the ZAP are listed under the alerts tab.
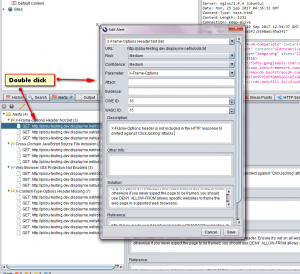
We can see details of each attack and its response by selecting them. More details can be viewed by double clicking on the vulnerability.
Report Generation:
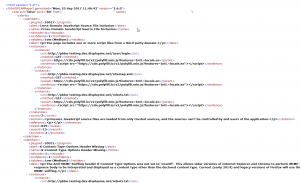
We can generate different types of reports from ZAP tools >> Reports. The most common types of reports generated are HTML report, XML report and Markdown report.
Finally, it should be clearly noted that the scanner detected vulnerabilities and its hazard levels may not correspond with the reality.
REFERENCES:
- http://toolsqa.com/software-testing/security-testing/
- http://www.optimusinfo.com/security-testing-basics/
- https://methoddev.com/
- http://intersog.com/